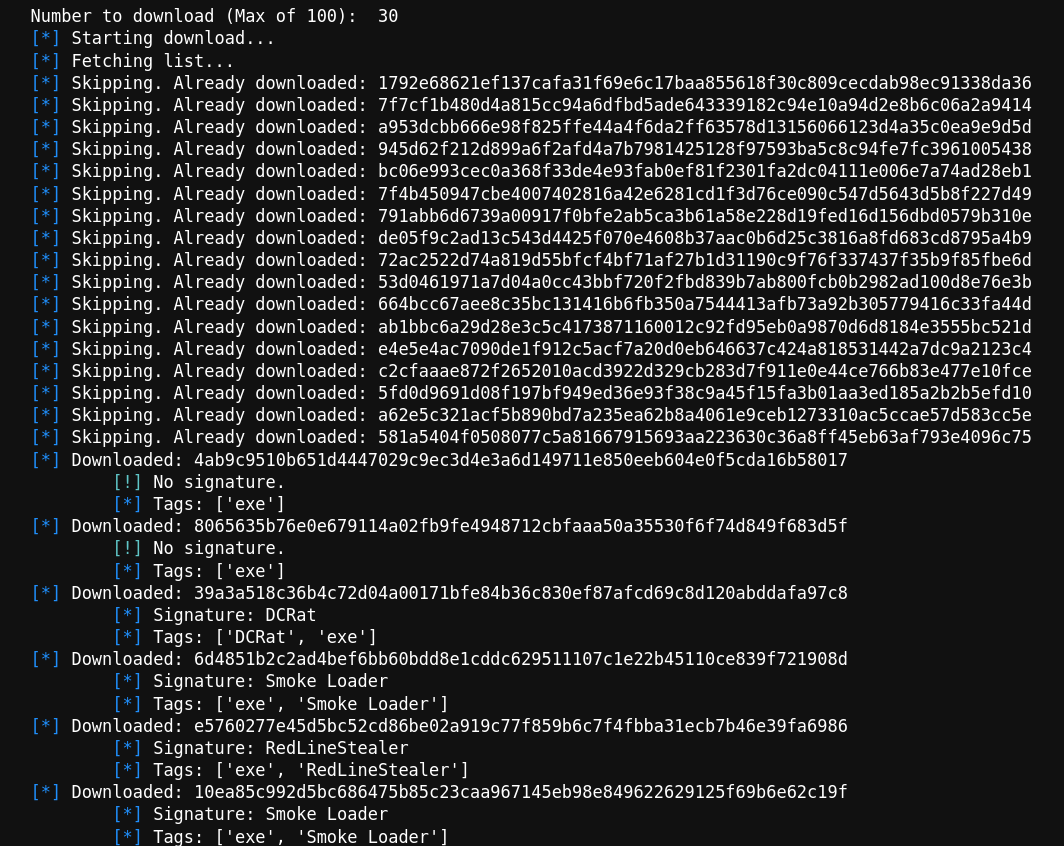
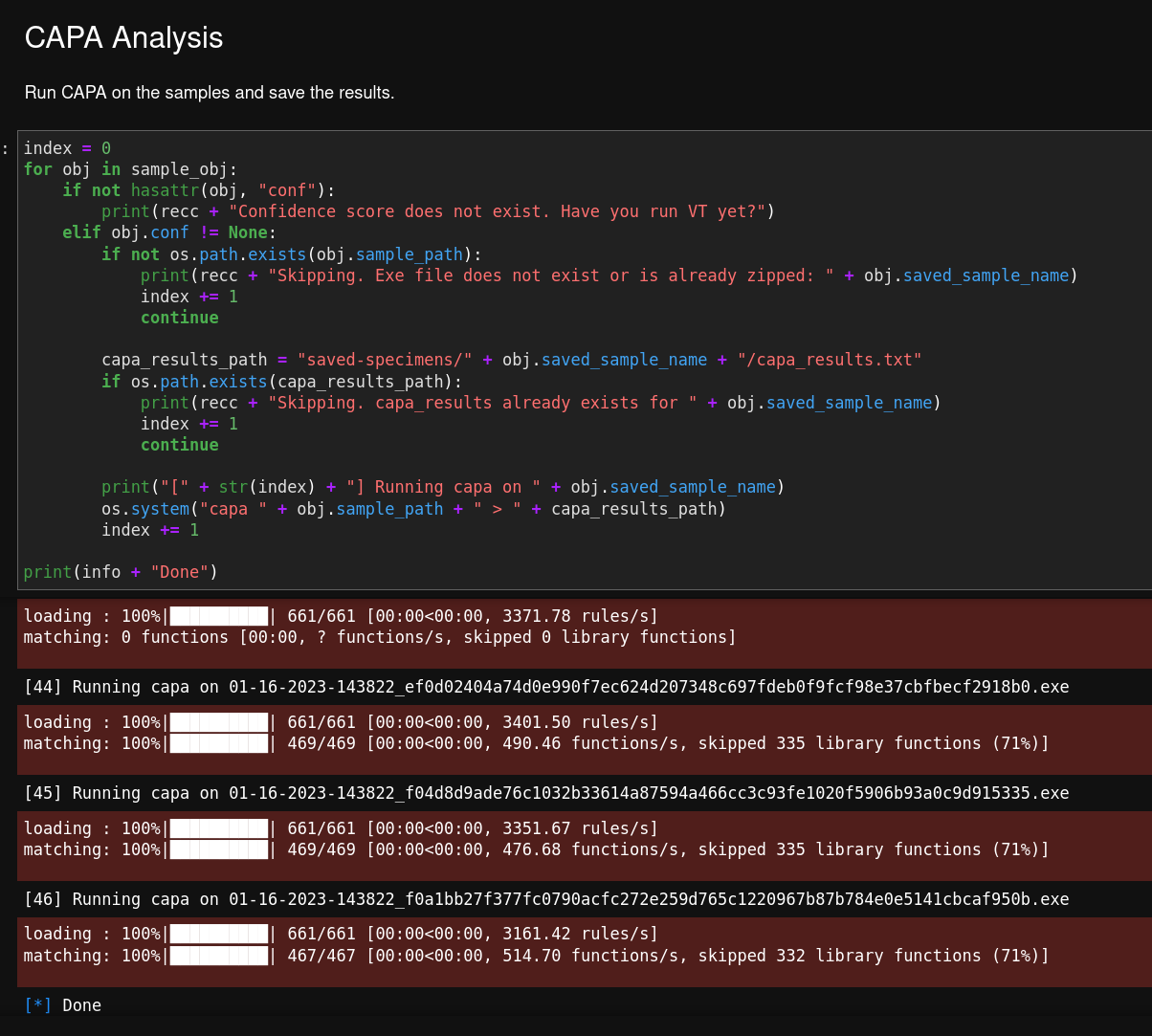
A hacker allegedly jailbroke Claude to hack Mexican government agencies, but key details remain unverified. Plus Claude Code and Copilot vulns, and Chinese AI firms stealing Anthropic's model.
Read more →AI, jailbreaks, and 150GB of unanswered questions